Authentication of patients in medicine via online system should be discussed ethically
Osaka University-led researchers review ethical issues regarding authentication of participants and patients in medical research/treatment using information and communication technology (ICT), proposing two-factor authentication
With the increase in data volume and dissemination of ICT, online system is being applied to medical research/treatment with high expectations. Not only exchange of research data, but also various modes of communication, including the informed consent process, are being promoted, and it is anticipated that individuals will proactively participate in research by their own volition, forming partnerships between researchers and participants.
At the same time, in order for individuals to participate in medical research/treatment without anxiety, ethical, legal, and social issues (ELSI) associated with the implementation of electronic methods for medical research/treatment should be addressed in earnest. However, research on authentication systems have mostly been performed from a technical perspective, so ethical issues, such as proof of user intent, have not yet been fully discussed.
In this study, the researchers pointed out that authentication systems for medical research/treatment need not only to prevent impersonation, but also to prove intent of research participants and patients.
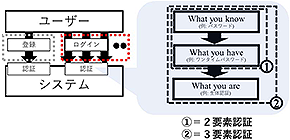
The researchers discussed authentication by separating “authentication at the time of registration” and “authentication at the time of login” (Figure). Focusing on the latter, the researchers clarified roles and set out methods of authentication. They discussed problems in current authentication systems from the ethical viewpoints of (1) respect for autonomy, (2) privacy protection, and (3) establishing a relationship of trust. Their research results were published in Frontiers in Genetics .
Lead author Atsushi Kogetsu said, “After much consideration, we proposed two-factor authentication as a workable solution, in which authentication is performed again using a one-off password after authentication via user ID and password. Some ICT specialists had proposed three-factor authentication, including biometrics, but we thought that biometrics had its own challenges and that current three-factor authentication might be cumbersome for users. Based on that, we also proposed the possibility of the necessity of biometrics and its requirements.”
This group’s achievements will contribute to building systems for medical research/ treatment in which individuals can participate free of anxiety. The research results will become a basis for discussion for ELSI not only about medical research/treatment using ICT, but also about ICT itself in various fields.
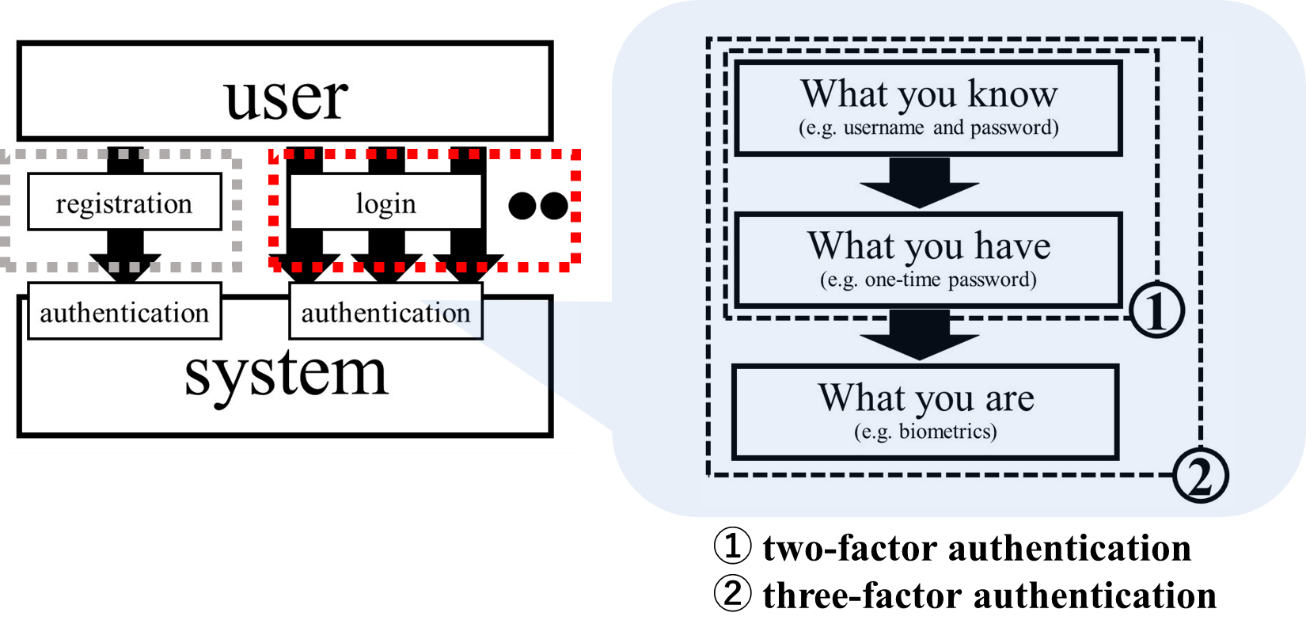
Figure: Authentication at the time of registration and login before participating in medical research, and our proposal on that topic
To participate in medical research, users need to register and login before using the system. Authentication is required for both registration and login, but considerations are necessary for each, separately. In this study, focusing on login (red frame), we propose two-factor authentication as a means of assuring that the user accesses the system of his/her own intent with preventing from impersonation. The arrows in the left diagram indicate the number of accesses.
(credit: Kogetsu, Ogishima & Kato 2018)
To learn more about this research, please view the full research report entitled "Authentication of Patients and Participants in Health Information Exchange and Consent for Medical Research: A Key Step for Privacy Protection, Respect for Autonomy, and Trustworthiness" a t this page of Frontiers in Genetics .
Related links
