Secure computation of genome data from multiple institutes with minimum invasion of privacy verified
NEC Corporation and a group of researchers led by Specially Appointed Professor NAKAYA Akihiro from Osaka University, in cooperation with Professor MATSUMURA Yasushi from Osaka University, demonstrated that a tool that allows analyzers to perform their own analysis methods using secure computation was good enough for practical use and that computer processing could be carried out at a practical speed.
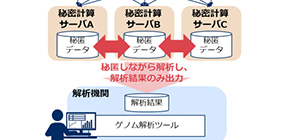
They conducted a verification test to apply secure computation, a technology that enables computation while keeping data encrypted, to a genome analysis system. This enables genome analysis while minimizing the risk of privacy invasion, promoting tailor-made medicine.
In recent years, genome analysis to clarify the relation between genomes and diseases is actively performed in order to develop effective drugs tailored to individual genetic makeup; however, because personal information used for data analysis is highly sensitive, it was difficult to share the data between medical and research institutes.
Secure computation that enables computation while keeping data encrypted is expected as a means for integration and analysis of personal genome and disease data from multiple medical and research institutes in its encrypted state. However, since the processing of conventional secure computation was extremely slow because of its complexity and systems for secure computation were difficult to create, it was not easy to apply secure computation to genome analysis.
In this study, the researchers applied NEC’s high-speed secure computation and development support tools to Osaka University’s genome analysis application DS Viewer, which performs integration and analysis of personal genome and disease data from multiple medical and research institutes, verifying the feasibility of performing safe genome analysis in a practical time frame.
They collected personal genome and disease data from multiple medical and research institutes to analyze mutation frequency in its encrypted state, disclosing tabulation results only when the results exceeded certain numbers in order to prevent personal identification by retrieval conditions.
As a result, they were able to perform integration and analysis of genome data of approximately 8,000 persons from different research institutions, obtaining the frequency of genomic variations by age within around one second. This demonstrates that it is possible to integrate and analyze personal genome and disease data in its encrypted state within a practical time frame.
They also confirmed that ordinary system engineers could embed secure computation protocols into Osaka University’s analysis application within a few days using NEC’s development support tools, which would otherwise take experts about a month. This shows that secure computation can be used for various genome analyses.
Figure 1
Related links
