The world’s first comprehensive security evaluation of Nostr, a decentralized social networking protocol
Speech at Black Hat USA 2025 Briefings, the most challenging international conference on attack prevention
- The world’s first comprehensive security evaluation of decentralized social networking protocol Nostr, which is used by approximately 1.1 million people was conducted.
- Identified critical vulnerabilities that could lead to post tampering, impersonation of user profiles, and developed countermeasures to prevent attacks.
- Speech was given at Black Hat USA 2025 Briefings, the most challenging international conference on attack prevention.
Outlines
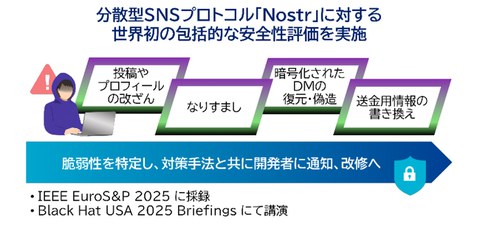
A joint research team consisting of the National Institute of Information and Communications Technology (NICT, President: Hideyuki Tokuda), the University of Osaka (President: Atsushi Kumanogoh), NEC Corporation (President and CEO: Takayuki Morita), and the University of Hyogo (President: Makoto Kosaka) has conducted the world's first comprehensive security evaluation of the decentralized social networking protocol Nostr, which is used by approximately 1.1 million people worldwide, by using the methodology of specification analysis, implementation investigation, and proof-of-concept. The research team identified critical vulnerabilities that could lead to post tampering, impersonation of user profiles, and the recovery of encrypted direct messages (DMs), and designed attack scenarios to exploit these vulnerabilities before attackers could. They also verified their effectiveness and developed countermeasures. The results of these security evaluations and the countermeasures were reported to each application developer, and improvements to the overall protocol design were demonstrated.
The research paper summarizing these results has been accepted for publication at the IEEE EuroS&P 2025 academic conference, and a speech has been scheduled to be given at the Black Hat USA 2025 Briefings, the most challenging international industrial conference in the field of attack prevention, and the results have been highly praised by both the academic and industrial communities.
Research Background
Until now, most social networking sites have been centralized, as exemplified by X, and it was common for platform operators to handle much of the work, from service provision to data management. However, in recent years, concerns about privacy and security risks, as well as algorithm modifications and manipulation of trend information that strongly reflect the intentions of platform operators, have led to decentralized social networking sites gaining attention as a new option. In a decentralized social networking site, services are provided through multiple servers managed by different operators, and users themselves can choose a trustworthy operator to use. It also offers a high degree of freedom in terms of privacy and security settings.
While apps using the decentralized social networking protocol Nostr are becoming increasingly popular, the complexity of its specifications and implementation has meant that sufficient security testing has not been conducted. Therefore, immediate action was needed as nobody had known when hackers would attack.
Research Contents
In this research, the researchers conducted a comprehensive security evaluation of the decentralized social networking protocol Nostr and its popular client application using methods of specification analysis, implementation investigation, and proof-of-concept (see Fig. 1). They identified that a combination of structural issues, such as a lack of coordination between multiple protocol designs, creates serious vulnerabilities that could lead to the post tampering, impersonation of user profiles, the forging and the recovery of encrypted DMs, and the alteration of remittance information. They designed eight specific attack scenarios to exploit these vulnerabilities ahead of attackers and verified the effectiveness of the attack scenarios using proof-of-concept code written in Python.
The results of these safety evaluations were reported to each app developer in June 2023 and January 2024, and collaboration began. At the same time, the research team proposed countermeasures to avoid attack scenarios and identified improvements to overall protocol design. Currently, these countermeasures are being implemented in stages through patch application and functional improvements to major client apps.
Fig. 1 Safety evaluation of Nostr
Credit: Takanori Isobe
Future Developments
Based on the results of the research to date, the research team will continue to evaluate other decentralized social networking apps and work to improve the safety of next-generation social networking sites.
Notes
- A speech, “Not Sealed: Practical Attacks on Nostr, a Decentralized Censorship-Resistant Protocol,” was given at Black Hat USA 2025 Briefings (URL: https://www.blackhat.com/us-25/briefings/schedule/index.html#not-sealed-practical-attacks-on-nostr-a-decentralized-censorship-resistant-protocol-45726 )
- The article, “Not in The Prophecies: Practical Attacks on Nostr,” was published in the 10th IEEE European Symposium on Security and Privacy (EuroS&P) 2025.
Analysis Methods and Details of the Results
In this study, the research team conducted security analysis and safety evaluation of Nostr using the following methods and identified the risks arising from the interactions of each sub-protocol.
1. Specification analysis The research team investigated all 56 functions described in the Nostr specification (as of December 6, 2023) and found that its integrity could potentially be compromised by a combination of NIP-01, NIP-04, NIP-46, and implementation flaws.
2. Implementation investigation
The research group conducted static and dynamic testing on five major clients, including iOS, Android, and Web, and discovered vulnerabilities in signature verification flaws in multiple clients.
The implementation flaw in link preview mechanism for encrypted DMs was identified and proposed a method to efficiently restore encrypted DMs by combining it with cryptography that is not tamper-resistant (AES-CBC).
3. Proof-of-concept The research team designed eight attack scenarios (see Fig. 2) by combining the seven identified categories of flaws, including signature forgery and plaintext recovery, and verified them by using Python proof-of-concept code.
This security analysis identified the following vulnerabilities:
Impact on authenticity: The Nostr specification did not have a mechanism to verify whether the public keys of the data sender and receiver were genuine (public key authenticity). The team identified this flaw in the specification and discovered that client applications connecting to the Nostr network are vulnerable to simple public key substitution attacks.
Impact on integrity: It has been shown that the lack of signature verification makes it possible to arbitrarily tamper with or forge profiles and posts. They also demonstrated that by reusing encryption keys between subprotocols, encrypted DMs can be tampered with and forged to any content.
Impact on confidentiality: By utilizing the automatic execution of link previews on the receiving device and the non-tamper-resistant nature of CBC mode, they confirmed that it is possible to obtain the plaintext and confidential URLs of DMs without user interaction.
The results of these security evaluations were reported to each application developer in June 2023 and January 2024, and collaboration began. As fixing methods, the introduction of a public key verification method, signature verification, and design guidelines for securely linking media acquisition mechanisms were proposed, and improvements to the overall protocol design were identified.
Improved countermeasures proposed
1. Mandatory signature verification for all events
2. Applying a message authentication code or authentication cipher to encrypted DMs
3. Disable link preview mechanism on the receiving device and generate previews on the sending device
4. Providing public key verification methods (Out-of-band authentication, Key Transparency, etc.)
These measures are being implemented in stages by applying patches and improving functionality to major clients.
Fig. 2 Main attack scenarios designed by the proof-of-concept
Credit: Takanori Isobe
